With the rapid development of social digitalization, as a key point connecting schools and digital cities, digital campuses are still an important link in the construction of "Digital China". "Digital campus" uses 4C (computer, communication and network, automatic control, IC card) technology to electronically manage campus and share resources through the network. The campus all-in-one card system applies radio frequency card technology and fingerprint recognition technology to the digital campus system. As an electronic identity carrier, the IC card uses fingerprint recognition technology for identity authentication, thereby facilitating teachers and students to automatically complete such tasks as borrowing / returning books, consumption, exams, and attendance And other activities related to their identities to improve the level of campus management. In this paper, a radio frequency card and fingerprint identification technology are used to design a campus card system.
1 Digital Campus and One Card System
Based on the "traditional campus", the "digital campus" uses advanced informatization methods and tools to realize the digital space of the campus, thus dividing the time and space of the real campus. It is based on the network and realizes all informationization of environment (including equipment, classroom information, etc.), resources (such as books, lecture notes, courseware, etc.) and activities (including teaching, learning, management, service, office, etc.). The characteristics of the digital campus are mainly reflected in three aspects: networked, intelligent and personalized.
All-in-one card system realizes highly networked, intelligent and informatized user units, improves unit management efficiency, adopts advanced radio frequency card technology, combined with the advantages of computer networks in data retrieval, communication, collection, etc. Responsible for many management functions such as employee work permit and time card. It comprehensively applies the current network technology, IC card technology, data management and other advanced computer technologies, and has the ability to improve the unified management of the school's personnel and finance, and realize the functions of identity recognition, electronic currency, electronic transactions on campus. The one-card system has been widely used in many colleges and universities abroad. Although some domestic enterprises and colleges have implemented the one-card application project in recent years, most of them are concentrated on consumption and book management. There is no in-depth research. The integration of multi-purpose systems has always been on the surface, so the research work of the card system has a broad market.
2 Application of radio frequency card in digital campus
2.1 RF card
Radio frequency cards are also called non-contact IC cards and inductive cards. It successfully combines radio frequency identification technology and IC card technology to solve the problems of passive and non-contact IC cards. It is a major breakthrough in the field of electronic devices. The radio frequency card is composed of an IC chip and an induction antenna, and is completely sealed in a standard PVC card. The radio wave between the radio frequency card and the reader is usually used to complete the read and write operations. The operation is convenient and fast, with strong anti-interference ability, high reliability, good security, and is suitable for one card and multiple uses.
2.2 RF card reader
If an application system (application software) wants to read and write data in a contactless data carrier (transponder), it requires a contactless reader as an interface. The data is read and written through radio waves between the two. Because the radio frequency card itself is a passive card, the signal emitted by the reader when reading and writing the card is composed of two parts: one part is the power signal. After the signal is received by the card, it generates an instantaneous energy with its own L / C Provides the work for the chip; the other part is the instruction and data signal, direct the chip to complete the reading, modification, storage, etc. of the data, and return the signal to the reader.
The reader mainly completes the reading and writing operations on the card, and the powerful ones can also perform data processing. Almost all terminals in this system need to use a reader, so it plays an important role in the application system. The card reader software mainly completes the authentication, reading and writing functions of the RF card, and displays the corresponding information according to the needs of the user, and has the necessary setting functions. The authentication key of the card adopts a unified fixed read key, and the write key is stored in the PSAM card through DES encryption.
In order to realize the security and confidentiality of the key, the system completes the identity authentication and various encryption and decryption processes with the user card through various master keys stored in the SAM module or SAM card. The physical structure of the SAM card is the same as the ordinary CPU card, but its difference is that the main functions of the operating system COS are symmetric encryption and decryption operations (DES operations) and key storage and management functions. After the key is written into the SAM card by the card issuing system, it is placed in the card reader to complete the mutual authentication of the card reader and the card. Once the key stored in the SAM card is written, it cannot be read and cannot be modified, and can only be used for encryption and decryption calculations.
3 Application of fingerprint recognition technology in digital campus
3.1 Introduction to fingerprint recognition technology
The texture caused by the uneven skin on the finger surface is the fingerprint. These patterns vary from person to person in patterns, breakpoints and intersections. In the recognition process, they rely on these unique "features" to verify his true identity by comparing his fingerprint characteristics with pre-stored fingerprint characteristics. Fingerprint is one of the biological characteristics of human body, with uniqueness, stability and non-reproducible, non-portable, non-forgeable characteristics_2J. As a means of identity authentication, fingerprint identification technology has many advantages such as carrying around, good security, convenient collection, low cost, small product size, fast recognition speed, good product stability and difficult imitation technology. There are two ways to apply fingerprint identification technology in digital campus:
(1) Store the cardholder ’s fingerprint (encrypted) on the IC card, and install a fingerprint recognition system on the IC card reader. When reading the information on the IC card, read in the cardholder ’s Fingerprint, by comparing the fingerprint on the card with the fingerprint of the cardholder to confirm whether the cardholder is the true owner of the card. This method occupies more storage units in the IC card and has less dependence on the network.
(2) Store all user fingerprint information on the host system database. Only the cardholder ’s fingerprint ID is stored in the IC card. After the card reader terminal reads the card, collect the cardholder ’s fingerprint information and the back-end database The fingerprint information corresponding to the fingerprint ID is compared to confirm the identity of the cardholder. The IC card resources used in this way are few and highly dependent on the network.
3.2 An automatic fingerprint recognition system algorithm based on the direction information of the line
With the continuous improvement of system security and robustness requirements, the original algorithm becomes difficult to meet practical requirements. Aiming at the problems of high rejection rate, easy rotation and translation, an automatic fingerprint recognition algorithm based on the direction information of the lines is used in this paper. The system has two functions: one is the collection process, that is, the establishment of a large-capacity fingerprint library; the second is the matching process or identification process, that is, randomly identifying a fingerprint. The system block diagram is shown in Figure 1.
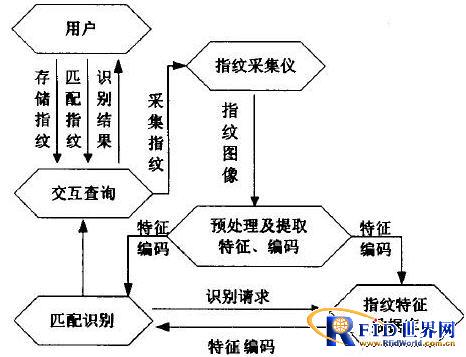
Figure 1 Block diagram of fingerprint identification system
In the unrepaired refined fingerprint image, there is a lot of noise. There are:
(1) When the finger is dry, there will be a lot of intermittent lines in the fingerprint image. And the distance between the two points is very small, there is no line.
(2) When the finger is wet or dirty, there will be more lines and lines on the fingerprint image, lines that should not be connected are stuck together. In addition, the two points are the branch points of the line, the distance between the two points is approximately equal to the average line spacing, and the line between the two points is approximately perpendicular to the direction of the line of its local area.
(3) Short lines: The characteristic is that the lines between two points are short but they are not regarded as isolated points.
(4) Hole shape: The characteristic is that the distance between two points is very small, and the direction of the line between the two points and its local area lines are approximately parallel.
(5) Burr: The characteristic is that a pair of end points are connected to the bifurcation by lines, and the distance between the two points is relatively close. Therefore, first of all, image preprocessing is performed on the collected fingerprints, that is, the fingerprint image is subjected to line repair and denoising to eliminate most random noise such as isolated points and short lines. The literature proposes specific fingerprint image preprocessing.
The details are mainly determined by its position and orientation. The conventional detailed feature extraction algorithm is to first refine the image, then repair the lines, and finally extract the detailed feature points. The purpose of fingerprint enhancement is to improve the clarity of the lines, such as separating the lines that are stuck together, connecting the broken lines, smoothing the edges of the lines, and so on. However, when the fingerprint image cannot be repaired, the detailed feature points extracted by conventional algorithms contain a large amount of pseudo-feature information. To remove the pseudo feature points, you can study the cause and distribution of the pseudo feature points, and then design the corresponding improved algorithm.
According to information and experimental observations, fingerprint lines and detail feature points have the following characteristics:
(1) Except for individual areas, the change of fingerprint lines is relatively gentle, and the width between adjacent lines is approximately equal.
(2) At a resolution of 500dpi, there are generally only detail feature points with a distance greater than 8 pixels in the fingerprint image.
(3) There is basically no structure with mutations such as burrs and cross-links in fingerprints. Therefore, structures such as the two end points of the lines that are very close together and the cross lines of the lines should be deleted directly.
The improved algorithm is defined as follows:

The fingerprint matching method based on the curvature of the line is to compare the distance between the point on the line and the end of the line in the two images, that is, to compare the curvature of the two lines, to determine the similarity of the two lines, so as to determine the reference point pair . Because the rotation and translation of the image does not affect the matching result, this method can better reflect the shape of the line, and the matching is more accurate.
3.3 Fingerprint recognition terminal
The fingerprint authentication device is a single-chip microcomputer based on a digital processor (DSP), which completes complex fingerprint recognition tasks that cannot be completed by a general single-chip microcomputer. Its physical composition is shown in Figure 2.
As the core of fingerprint application system, fingerprint authentication device mainly completes fingerprint collection and fingerprint matching. In this system, the module performs asynchronous serial communication with the main control unit through the RS232 port to realize fingerprint collection, feature data generation, and matching of two fingerprint images. The processed fingerprint feature data numbers are stored in the data memory. The fingerprint identification terminal is mainly used for attendance and test identity authentication in the campus card system. It is used in conjunction with the radio frequency card reader terminal. The ID number is provided by the information stored in the radio frequency card.

4 Campus card system based on radio frequency card and fingerprint identification technology
The campus all-in-one card system realizes digitization of resources, transmission network, intelligentization of user terminals, and automation of management and settlement. The system realizes the connection with the banking system, automatically transfers bank deposits to campus cards to meet various consumptions on campus; at the same time realizes personal identity authentication; also realizes the link with the school management information system to realize the basic information for students, faculty and staff Inquiries, and comprehensive inquiries for leading macro management.
4.1 System structure
The system is divided into campus management and bank management according to its different behavior subjects. Campus management realizes the issuance, replacement of cards, account cancellation and card consumption, and identity recognition management of IC cards. Bank management mainly completes functions such as card opening, depositing, depositing, card replenishment, account cancellation, and blacklist management. The bank-managed front-end machine is connected to the campus-managed financial center server. When the cardholder loads the amount from the debit card account to the IC card, on the day of the deposit, the bank will summarize the total amount of all accounts and all The total amount of the account load is sent to the settlement center of the campus for reconciliation. At the same time download the file to the designated outlet, the next day from the outlet to transfer the total consumption yesterday to the school account. The report of the blacklist and the removal of the report are first carried out by the school and transmitted to the bank in real time.
4.2 "Campus Card" data transmission process
The data transmission process of the "Campus Card" is divided into five levels, namely the collection, forwarding, transmission, processing and application of transaction data. The upload transaction data collected by various terminal devices enters the trunk of the All-in-one Card network through serial communication and networking equipment, and then uploads to the main server of the "Campus All-in-One Card Management and Settlement Center" to ensure the real-time and integrity of the data.
4.3 Management Organization System
The "Campus Card" system adopts a three-level management model. The top-level management is the "Campus Card Management and Settlement Center"; --- level management is the "management sub-center" of each campus; the third-level management is a part-time administrator of the department.
4.4 System application scope
The campus card in the "Campus Card" system uses a non-contact encryption IC chip and bank magnetic stripe compound method, so that the campus card has both bank financial services and payment functions outside the campus, as well as various consumption and campus management on campus The main functions include identity verification, deposit consumption and information query.
4.5 System topology structure
The topology structure of the campus part of this system is shown in Figure 3.
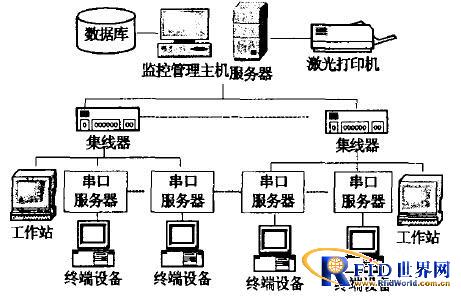
Figure 3 The topology of the campus part
5 Summary
The research results in this article are suitable for the needs of modern digital campus informatization, and can achieve a win-win strategy for banks and schools, with the prospect of universal application. However, the author's research in this field has just started. In the future research work, there are still many problems to be studied, such as: the research of emerging key algorithms; fingerprints for small area fingerprints, residual lines, and dry and wet fingers Research on recognition algorithms, etc., all need to be studied in depth.
O Ring File Folder,Portable O Ring File Folder,Large Capacity O Ring File Folder,Plastic O Ring File Folder
TAISHAN JINRI STATIONERY PLASTIC CO.,LTD , https://www.jinri-folder.com